If you’re responsible for an IT setup then a firewall (or even more than one) is essential to keeping your data protected against cyber attacks. But what actually is a firewall and how does it work? Read our article below for a clear explanation on how a firewall keeps your IT safe.
What is a firewall?
The term ‘Firewall’ actually comes from the building industry where it refers to a wall designed to stop fire spreading from one part of the building to another. In the same way, a firewall prevents certain traffic transferring between different devices on a network.
A firewall can either be a software application or a hardware device physically connected to a server. Generally speaking, a physical hardware firewall will be more sophisticated than the software equivalent, but that doesn’t mean they provide more protection. A firewall controls and blocks traffic from reaching computing devices on a network, without compromising their performance, protecting them from attacks.
How does a firewall keep your personal PC safe?
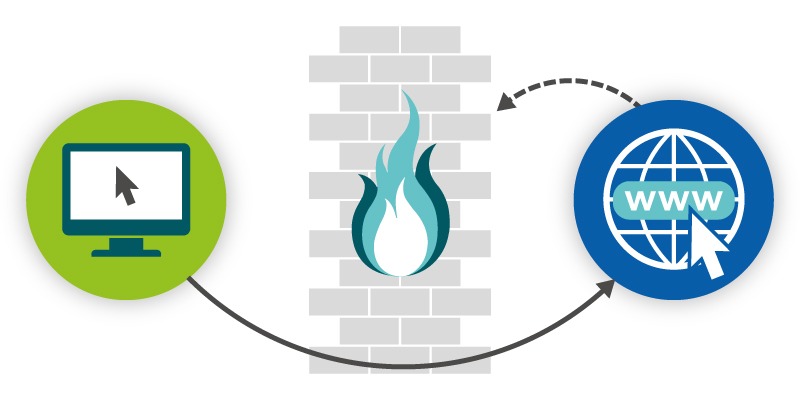
Typically, the firewall used to protect a personal PC, at home or at work, is a straightforward software application blocking any and all traffic coming from the general internet coming back to the PC.
The firewall will allow all outgoing requests and traffic from the PC to the internet, and it will also allow replies to these requests. Firewalls can also be configured to block certain outgoing requests if you want to limit users PC use (for example, restricting access to unnecessary websites at work).
Since the firewall blocks all incoming traffic, it also blocks any potential attacks someone might be targeting you with.
How does a firewall keep a server safe?
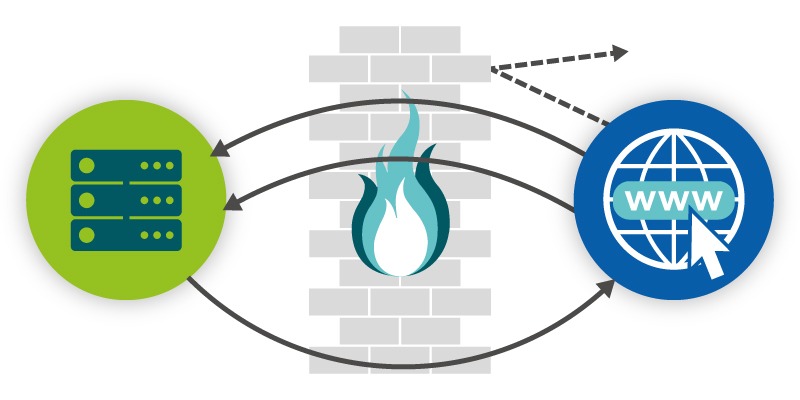
As well as allowing outgoing request and replies to those requests, a company’s server needs to be accepting incoming traffic and requests, so they can service their users, which is a more sophisticated firewall setup. This could still be a sophisticated software application, or this is where you might deploy a physical piece of hardware.
Traffic a business would want to allow through the firewall to access their server could include SSL (Secure Sockets Layer) protected web traffic, SSH, email or FTP, and other encrypted traffic that is typically safe.
Conversely, MySQL traffic (on port 3306) is blocked by a lot of firewalls since MySQL lacks strong encryption, therefore blocking this traffic helps to prevent a potential hacker from reading sensitive data.
All outgoing traffic from the server is allowed through the firewall. And, again, you can setup rules which block and filter certain outgoing traffic.
All of these restrictions placed on incoming or outgoing traffic is done by the firewall opening and closing certain ports.
Advanced firewalls can also actively monitor traffic
If your business needs a higher level of security, you can opt for an advanced firewall which does more than just passively block set types of traffic, and instead will actively monitor the traffic passing through the firewall.
This allows for protective features including intrusion prevention and intrusion detection, where the firewall will detect and block threats as they come in, allowing for a wider variety of traffic to pass through the firewall, while providing comprehensive security.
If you’re currently researching data centre solutions, either colocation or cloud, make sure any potential providers can provide the level of cyber security you need. At Redcentric our managed firewall service utilises next-generation firewall technology from WatchGuard, as well as our specially designed firewall infrastructure. You’ll also have a team of experts managing and maintaining, so no cracks ever appear in your firewall, without you having to lift a finger. To learn more, see our information on Redcentric’s managed firewall solutions, or talk to one of our cyber security experts.